Business management will always have two perspectives on risk.
Traditionally, the goal is to find the perfect balance of risk and reward. Sometimes, a business will accept a more significant threat risk for a chance of growing quickly. At other times, it switches to controlling threats with slower growth. The operational risk management perspective is the latter, being more risk-averse and focusing on protecting the business from operational risk events.
What is operational risk management?
An operational threat risk is a loss resulting from ineffective or failed internal processes, people or systems, or external events that could disrupt the business operation.
The losses can directly or indirectly impact financials, a schedule, or business performance. For example, a poorly or untrained employee may lose a business opportunity (financial) or indirectly a business’s reputation through slow (schedule) or poor customer service (performance).
Operational threats refer to threats to business operations and the processes senior management uses to implement, train, and enforce procedures, policies, and guidance.
Examples of operational threats
Threats permeate every business and business process. The goal is to focus on the threats that impact the company and hold those who manage the threat accountable.
Examples of operational threats:
- Employee performance
- A data breach of personal data (a cyber risk)
- Business processes
- Physical events such as fires and floods
- Internal and external fraud
- Failing to achieve regulatory compliance
How does operational risk management work?
When dealing with operational risk, the business must consider every aspect of its objectives. Operational risk management attempts to reduce threats through risk identification, assessment, measurement, mitigation, monitoring and reporting while determining who is accountable for the threat. The goal is to avoid, transfer, accept, or control and mitigate all threats to an acceptable level.
Four principles guide the stages:
- Accept threats when the benefits outweigh the costs
- Accept no unnecessary threats
- Anticipate and manage threats by contingency planning
- Make decisions on a threat at the right level of accountability
Risk Identification
Operational risk management begins with risk identification and threat analysis. A framework should be used or developed to ensure completeness as a best practice. An example of the framework could be using a SWOT combined with a PESTLE for each of the 2 SWOT areas addressed: Weaknesses and Threats. This can be combined with a Strength and Opportunity analysis to provide an overall business picture.
Risk Assessment
Once the threats are identified, they are assessed using an impact and probability scale, as provided in GetRiskManager.
Measurement, Control and Mitigation
The threats are measured on a consistent scale and ranked against one another. Then, Risk control and mitigating measures (actions) are applied to each threat.
Monitoring and Reporting
Threats are monitored on an ongoing, timely basis to determine any changes, including if a threat is no longer applicable.
The threats and changes are reported to stakeholders, management, and the Board.
What’s the principal objective of operational risk management?
The primary objective of operational risk management is proactively protecting the business by managing potential risk events.
A framework will help provide the internal risk control processes as mentioned above. One approach to understanding how the process investigates the business risk is by organising operational threats into categories defined by a PESTLE, e.g.:
- Political – the focus is on the role of governments in shaping the industry and includes elements such as tax policies, changes in trade restrictions, tariffs, and the stability of national and international governments
- Economic – centres on the economic conditions within which a business operates, including interest rates, inflation rates, gross domestic product, unemployment rates, levels of disposable income, and the general growth or decline of the economy
- Social – looks at trends in demographics such as population size, age, and ethnic mix, as well as cultural trends and customer activism
- Technological – focusing on improvements in products and services that are provided by new or improved technologies, including, for example, changes in the speed of new product development, increasing automation, and advancements in service delivery
- Environmental – involves the physical conditions within which a business operates, including factors such as natural disasters, pollution levels, and weather patterns
- Legal – centres on how the law and courts influence business. Examples include employment laws, health and safety regulations, discrimination laws, and antitrust laws
Additionally, a business may also wish to look at people.
People include employees, customers, suppliers, and other stakeholders. Employee threats include human error and intentional wrongdoing, such as fraud cases, breaches of policy, insufficient guidance, poor training, and poor decision-making.
Monitoring and controlling social media threats is currently one of the most significant areas of concern. Outside of the business, several operational threats include people. For example, social media threatens employees, customers, suppliers, and other stakeholders.

How many steps are in the Operational Risk Management process?
Risk management is a five-step process. All five steps are critical and must be implemented.
Step 1: Risk Identification
Risk identification starts with understanding a business’s objectives. Threats are anything that prevents the company from achieving its objectives. Threats must be identified so these can be managed.
Step 2: Risk Assessment
Risk assessment is the process of rating risks on impact and probability. The outcome is a ranked listing of known Inherent Risks.
Step 3: Managing Risk
The managing risk step involves choosing a path for managing the threats. There are four options: Transfer, Avoid, Accept, and Reduce.
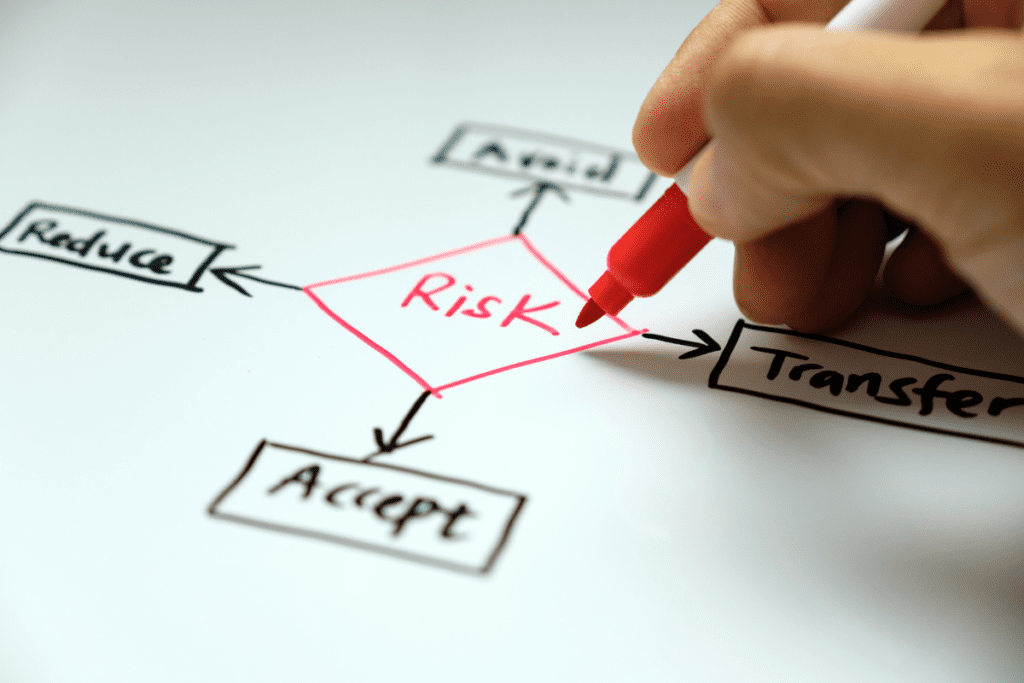
Transfer
Transferring shifts the risk to another organisation. The most common methods for transferring are outsourcing and insuring.
When outsourcing, management cannot wholly transfer the responsibility for managing the threat risk.
Insuring against the threat transfers some of the financial impacts of the risk to the insurers.
Avoid
Avoidance prevents the organisation from entering into a risky situation. For example, when choosing a Third Party for a service, the business could accept a higher-priced bid if the lower-cost proposal lacks sufficient experience.
Accept
When comparing the cost of managing the risk event to the cost of impact, a business could accept the risk and proceed with the risky choice.
Reduce (Control and Mitigation)
Control actions are the processes the organisation puts in place to decrease the probability of the threat occurring.
Mitigation actions lessen the impact of the threats that occur.
Step 4: Implementation
Implementation is next once the risk control and risk mitigation decisions are made.
The control and mitigating action are designed to meet the threat in question. The action rationale, objective, and activity should be documented to communicate clearly to stakeholders and subsequently implemented. The actions should focus on control and mitigating measures over administrative policies.
Step 5: Monitoring
Monitoring involves testing (by internal audit) the operational risk management framework for design suitability, implementation, and operating effectiveness. All the control and mitigating actions must be monitored, with any exceptions or issues raised and action plans established.
What are the issues and challenges of Operational Risk Management?
In many businesses, issues and challenges, such as competing priorities and a lack of understanding of the risk management value, affect the proper development of risk management systems programs. Some common challenges include:
- A perception is that a business does not have sufficient resources (financial, people, or systems) to invest in risk management
- The need to improve communication and education around the importance of risk management and the consequences of threats to the bottom line
- Increasing awareness across boards and other stakeholders to better understand risk management
- Inconsistent methods to measure and assess threats and then provide a view of a business’s risk profile, such as the Risk Matrix below
- Having a standard terminology that is conducive to successful risk management

What are the benefits of a robust Operational Risk Management program?
Establishing an operational risk management program helps a business achieve its strategic objectives while ensuring business continuity during operations disruptions.
Risk management demonstrates that the company is prepared for crisis and loss. Businesses that effectively implement a robust risk management process have competitive advantages, including:
- Better risk visibility for stakeholders
- Better-informed business decisions
- Improved performance
- Stronger relationships with customers and other stakeholders
- Greater external investor confidence
How to develop Operational Risk Management
As a business begins the process of creating an operational risk management framework, there are many areas the company should focus on, including:
- Promoting a business-wide understanding of the value of risk management
- Using technology to implement an approach to monitoring and managing risk
- Establishing an effective method for identifying principal risks in the business, continuously identifying and updating those risks and associated control and mitigation measures
- Focus on helping the business reduce risk exposure and encouraging activities where the potential benefits outweigh the threats
- Focus on understanding the threats to all functions in the business
Operational Risk Management Tools
Establishing an effective, robust risk management capability is essential to ensuring the correct business decisions. It’s a critical aspect of the Board and C-suite toolbox, leading to a competitive advantage.
Technology enablement, such as using GetRiskManager, increases the value risk management brings to the business.
Find out how GetRiskManager can help you manage, automate, and streamline your risk management program and turn your operational threats into opportunities to gain a competitive advantage by going to GetRiskManager.






