In business, risk management identifies, assesses, controls, mitigates, and monitors potential risks (negative and positive) to manage their consequence on an organisation.
This article focuses on risk identification.
What is the risk management process?
There are five steps to any effective risk management process:
- Risk Identification (this article)
- Risk Analysis
- Risk Assessment and Risk Evaluation
- Risk Control and Risk Mitigation
- Risk Monitoring
What is risk identification?
A risk identification process identifies and documents negative and positive potential risks that could keep or enable an organisation to reach its objectives. To do this, you must ask questions about every aspect of the business, such as – what could go wrong?
There are many ways to identify risks.
The most important thing is to be systematic and rigorous in the approach and use the right tools and techniques. The right questions should be asked to ascertain the correct possible risk sources. Once complete, all risks should be entered into a risk register.
Why is risk identification important?
Risk identification enables organisations to develop plans to manage positive or negative risk events before they arise.
The objective is to identify all risk events that could harm business operations, such as lawsuits, theft, technology breaches, and business downturns, and positive risks that, if managed correctly, could help an organisation achieve or exceed business goals.
When should risk identification be undertaken?
Risk identification should begin early in the business operation, i.e., during the start-up phase, when uncertainty and risk exposure are most significant and when risk management can have the greatest impact.
Identifying risks early also allows risk owners to act when risks are usually more straightforward.
Risk owners who execute early responses often reduce costs compared to addressing a significant risk and issue later in the project or business lifecycle.
What are the risk identification methods?
Risk Identification methods are established tools for analysing business operations (internal and external) and discovering threats and opportunities.
The most popular techniques in risk management are shown in the next section.

19 methods to identify risks
These are provided in alphabet order:
Affinity diagram
An affinity diagram organises information into categories based on their similarities.
Participants propose what they believe are potential company risks and file each response under a few categories. For example, they can be financial, schedule, or safety risks. This separates the risks into categories for expert review and organising the feedback. From there, the participants can assess, prioritise and address each risk.
Assumption analysis
Assumptions Analysis explores the accuracy of business assumptions and identifies risks to the business around inaccuracy, inconsistency, or incompleteness.
Bow Tie Analysis
Bow Tie Analysis identifies where new or enhanced controls may be worthwhile. It is a core part of risk management, particularly where there is a high level of risk or where control effectiveness is assessed as low.
Brainstorming
Brainstorming gathers people who are stakeholders in the business.
It allows participants to speculate ideas, share facts, consider the future business, and identify risk events.
Brainstorming is simply one way of identifying risks; the risk events listed may have come from those on the sharp end of the business who are more familiar with their day-to-day operations.
A brainstorming session can be run regularly to determine what stakeholders think the business’s most significant risks are.

Business plans
A business plan is a basic outline of the organisation and its needs. This includes material and labour needs, the timeline for the business, and any risks associated with it.
A detailed business plan may help understand its culture and what it takes to reach organisational goals.
It also informs stakeholders about what they’re investing in, tracks team progress, and offers a return on the initial investment.
Cause and Effect, Ishikawa, or Fish-bone diagrams
These diagrams are a way of searching for root causes, identifying problems, and comparing the importance of different causes.
Exploring the causes and continually asking why or how for each cause leads to better risk analysis and understanding of the problem.
Checklists
A risk checklist is the final risk identification step to ensure that common risks are not overlooked.
What is it?
Risk checklists are historical lists of lessons learned, previously identified risks, or risks realised in the past. They are meant to be shared among all stakeholders.

Delphi
The Delphi method takes its name from a religious sanctuary dedicated to the Greek god Apollo. Developed in the eighth century B.C., the sanctuary was known for divining the future and was consulted before all major undertakings.
The Delphi technique involves sending questionnaires to experts and stakeholders and compiling their responses without linking the opinions to those who suggested them.
The responses are then returned to the same group for further qualitative risk analysis or amendments.
Stakeholders and experts supply their opinions of risks anonymously without influencing one another.
Direct Observations (dynamic risk assessment)
Although not a specific technique for risk identification, direct observation has a prominent position. Establishing a culture of lifelong risk awareness is the best way for businesses to be prepared for any risk.
The personnel assigned are the first to sense when something is a threat or opportunity and take the necessary measures.
Direct observations can also be known as dynamic risk identification.
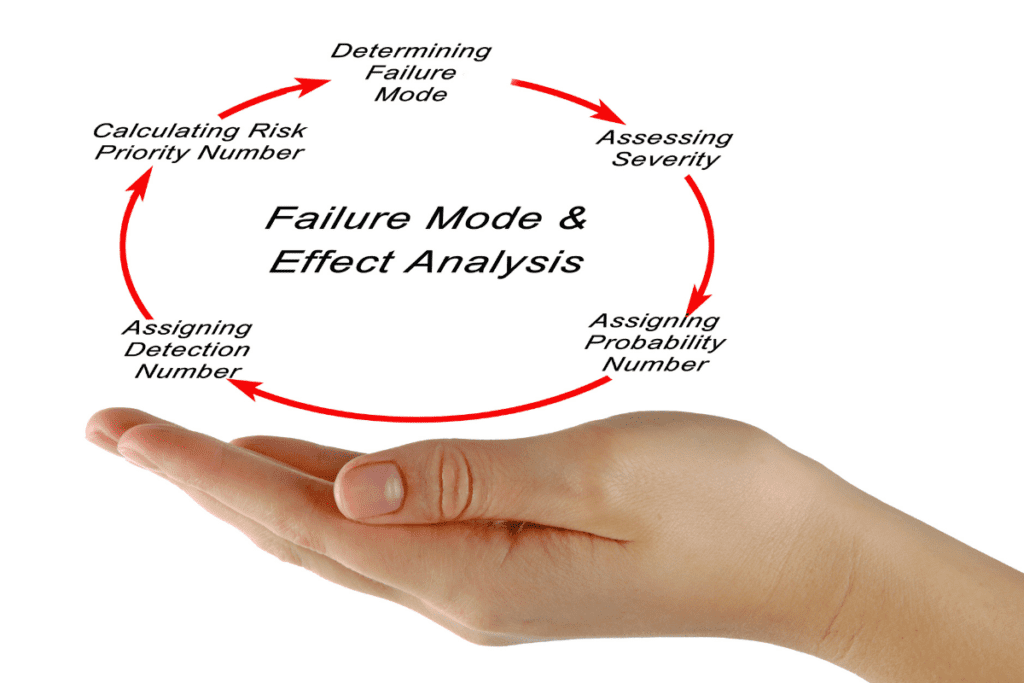
Failure mode and effects analysis (FMEA)
Failure Mode and Effects Analysis identifies failures that pose the most significant overall risk for a process, product, or service.
This risk identification technique identifies the following:
- Failure mode: How a product can fail, or deficiencies or defects
- Effect of failure: The consequences of a particular mode of failure
- Cause of failure: The causes of an observed mode of failure
- Analysis of the failure mode: Its frequency, severity, and chance of detection
Fault Tree Analysis (FTA)
Fault tree analysis (FTA) is a visual method to explore the causes of system-level failures.
It uses Boolean logic to combine a series of lower-level events. It is a top-down approach to identifying the component-level failures (basic event) that cause the system-level failure (top event).
Fault Tree Analysis consists of two elements:
- Events
- Logic gates: connecting the Events to identify the cause of the undesired event
Incident Analysis
Incident analysis methods are used in many different sectors and cover a range of specific techniques, including:
- Root Cause Analysis
- 5-Whys
- Incident Bow-tie
- Systematic Cause Analysis Technique (SCAT) Analysis
Interviews with stakeholders
Stakeholders are people with an interest in the business.
Interviewing them helps better understand what they believe are the most significant risks.
Stakeholders often invest significant resources in a business. They may provide an understanding of risk from an external perspective and help the company learn what concerns stakeholders have and how to address them.
Nominal Group Technique (NGT)
The NGT, or Nominal Group Technique, is a brainstorming method that offers a more detailed approach to the subject matter.
The participants write their ideas about the risks without discussing them with other members. Then, the team leader asks and collates views from each participant for their thoughts, removing overlapping risks.
NGT depends on honesty and teamwork and provides a more comprehensive approach than brainstorming. The participants discuss each item to ensure everyone understands them, and then you can work to prioritise each.
PESTEL analysis
PESTEL analysis is a risk monitoring process that identifies the Political, Economic, Socio-Cultural, Technological, Environmental and Legal risks in organisations.
PESTLE analysis may help assess the risk arising from the impact of external factors. This may include tax policy, employment laws, environmental regulations, trade restrictions, tariffs, reform and political stability.
PESTEL analysis can be used with many other forms of risk identification, for example, within SWOT analysis.

Requirements review
Requirements Review studies a business’s labour, material or financial needs.
It allows the participants to analyse requirements often and identify potential risks quickly.
The participants can complete a requirements review throughout the business timeline to understand risks and needs at each stage of the business lifecycle. During operation, requirements can change, which also may change the risk involved. For example, suppose a process requires twice as much material as initially speculated. In that case, the business’s financial risk rises because of additional costs.
Root cause analysis
A root cause analysis investigates previous business risks and how they relate to one another and the current project. The root cause can be a financial risk, old equipment, poor-quality materials, etc.
Finding the root cause allows the analysis to identify common business challenges and minimise them for greater business efficiency.
Scenario Analysis
In scenario analysis, different scenarios are created.
The scenarios are alternative ways to achieve an objective or analyse the interaction in a market sector, for example.
Any event that triggers a desired or undesired scenario alternative is identified as a risk.
Structured “What-if” Technique (SWIFT)
Structured What-If Technique (SWIFT) is a hazard analysis method that uses structured brainstorming with guidewords and prompts to identify risks quicker than more intensive methods like Failure mode and effects analysis (FMEA).
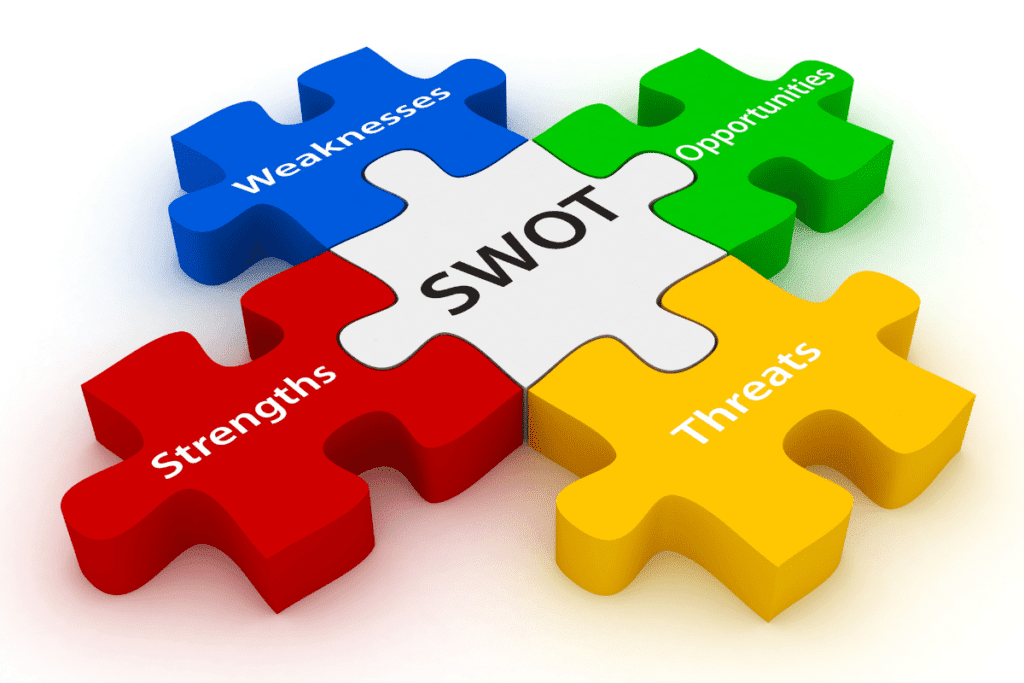
SWOT analysis
Strengths, Weaknesses, Opportunities and Threats (SWOT) analysis is a way to understand a business’s risks alongside other important factors.
A SWOT analysis can show why a business or project is worth investing in and helps the business better understand its ability to reach goals.
A SWOT analysis examines four factors:
- Strengths: where the business excels
- Weaknesses: where the business can improve
- Opportunities: where the business can improve, grow or expand
- Threats: risk for the company and how it can minimise those risks
Risk identification errors
There are some common mistakes in risk identification that many fall victim to when managing business risks. These include:
- Risks are not captured in one place
- Not identifying risks correctly
- Only using a single risk identification method
- The failure to recognise risks early to allow management of the risk
- Risks are not identified with appropriate stakeholders
- The failure to make all risks transparent and available to all stakeholders
- Not aligning risk identification with organisational goals
- A project, departments, other divisions, etc., creating their risk identification framework
- Risk identification analysis and practitioners are disconnected from the business
- Not considering opportunities
- Not making risk identification an ongoing process
What risk identification methods should I use?
There are many risk identification methods that businesses can use to protect themselves.
The best method depends on the specific business and its risks.
The responsible risk manager should evaluate the business and provide the most suitable methods.
If you are inexperienced in risk management and want an overview, GetRiskManager suggests using Brainstorming with a SWOT analysis. The SWOT is supported within each section by a PESTEL analysis.
Once complete, the risks are reviewed for further identification through a different method.
Conclusion
Businesses can use many risk identification methods to protect and grow, but choosing the most suitable method is essential.
